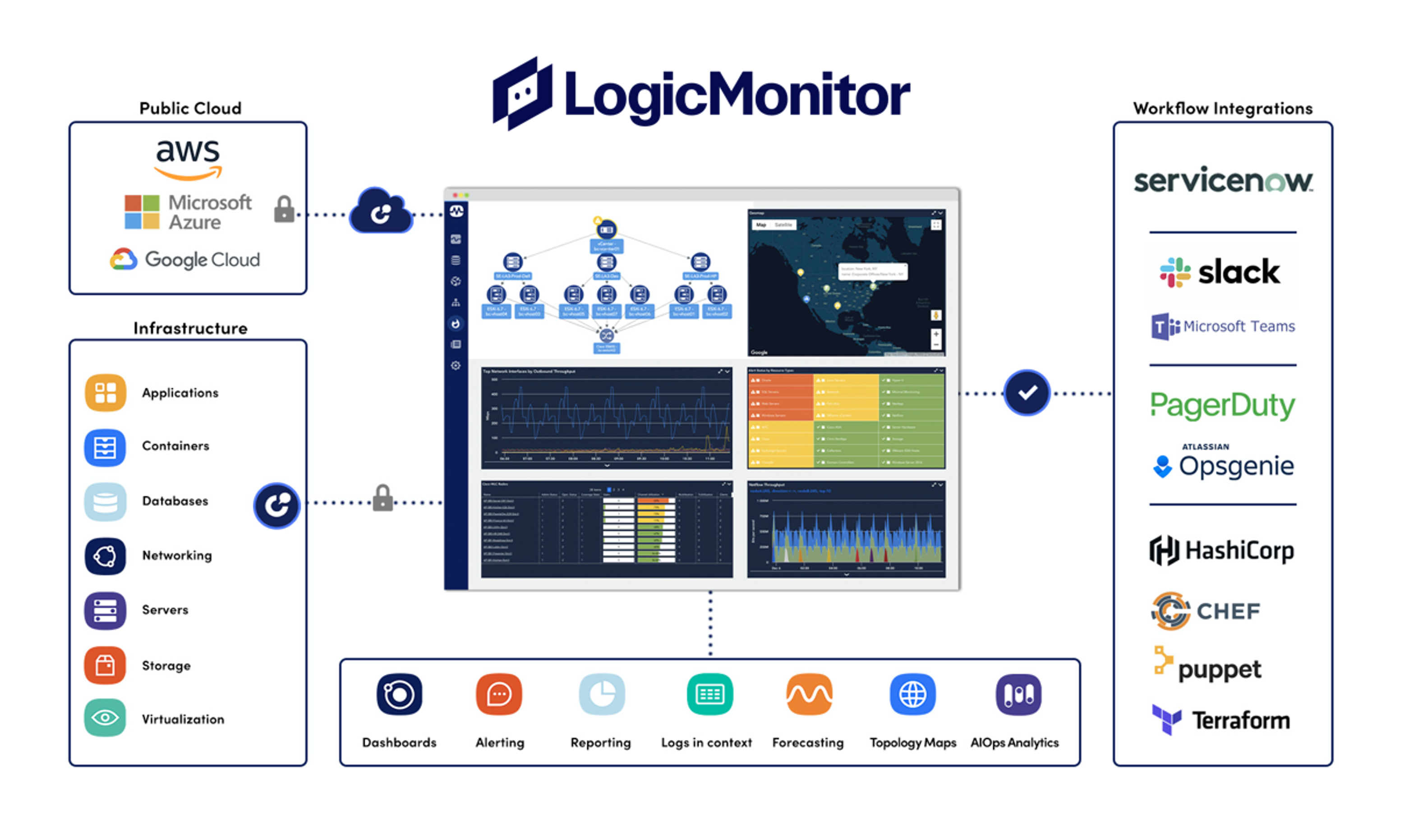
LogicMonitor: Cloud-based monitoring platform for uniform observability in heterogeneous IT environments
The modern IT landscape is complex and based on a wide variety of operationg models (on-premise, cloud, hybrid). By using a wide variety of monitoring tools, companies usually lack the integration and scalability needed to manage this complexity. LogicMonitor's observability solutions replace these tools with a unified monitoring platform. The result: more time, higher efficiency, lower costs and higher growth in business.
Discover what LogicMonitor has to offer:
LM Envision
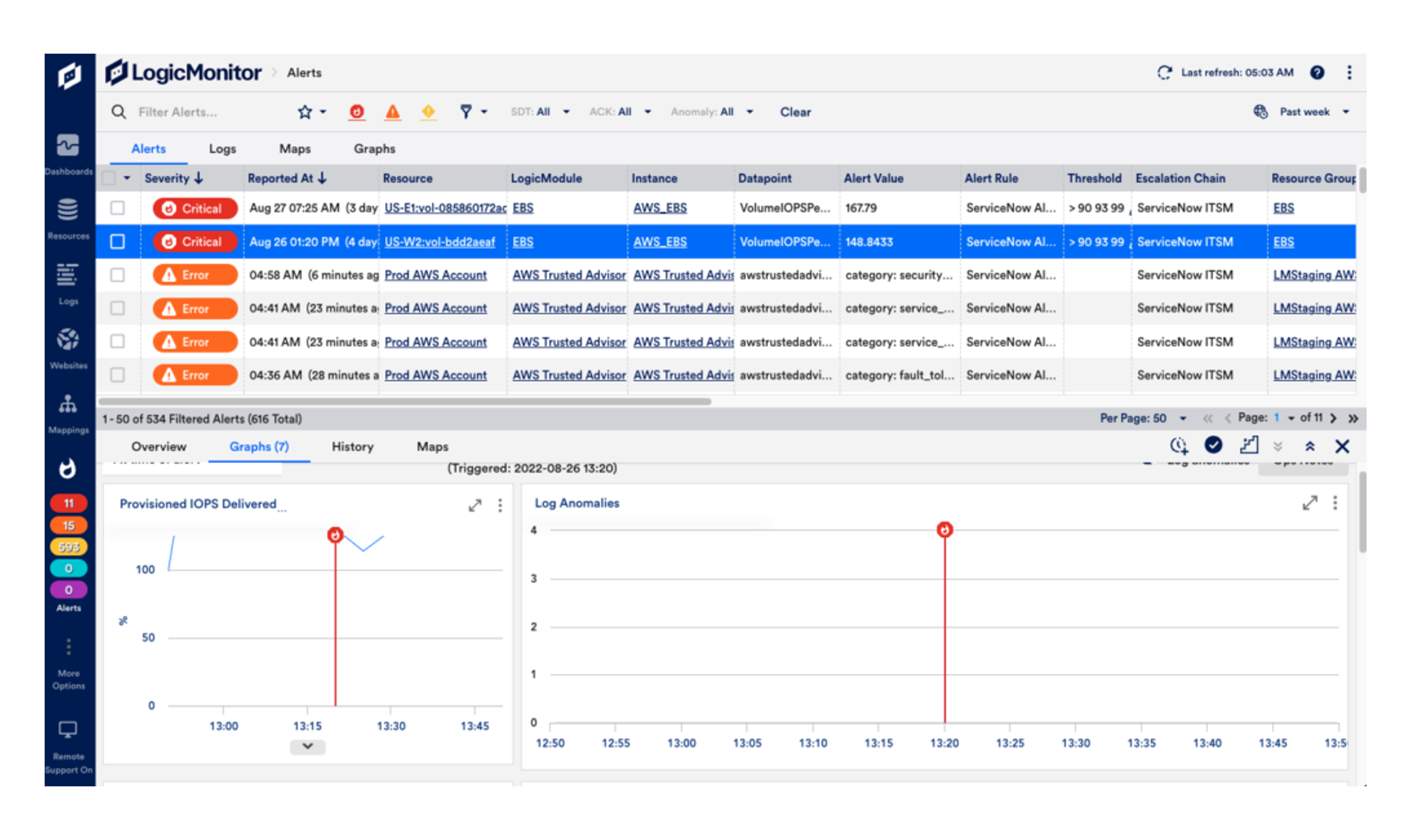
LM Envision is a SaaS-based unified-observability platform that enables organisations to adopt a cloud-enabled operating model as part of their digital transformation today, effectively addressing key business needs.
Finding your way through the IT jungle
LM Envision brings clarity to hybrid IT environments. Different IT and development teams can work together to solve complex problems. IT is able to innovate faster while optimising the operational efficiency of the critical IT services it provides.
LM Envision enables you to
• solve problems immediately based on a "single source of thruth" for all DevOps and ITOps teams,
• proactively gain insight into emerging anomalies through real-time analysis of IT data,
• reduce costs and risks through consolidated monitoring of IT infrastructures and applications,
• centralise functions that provide better scalability and innovation in the business on a single platform,
• use an AIOps early warning system to adress potential problems before thex even occur.
↑↓ Navigation: LM Logs
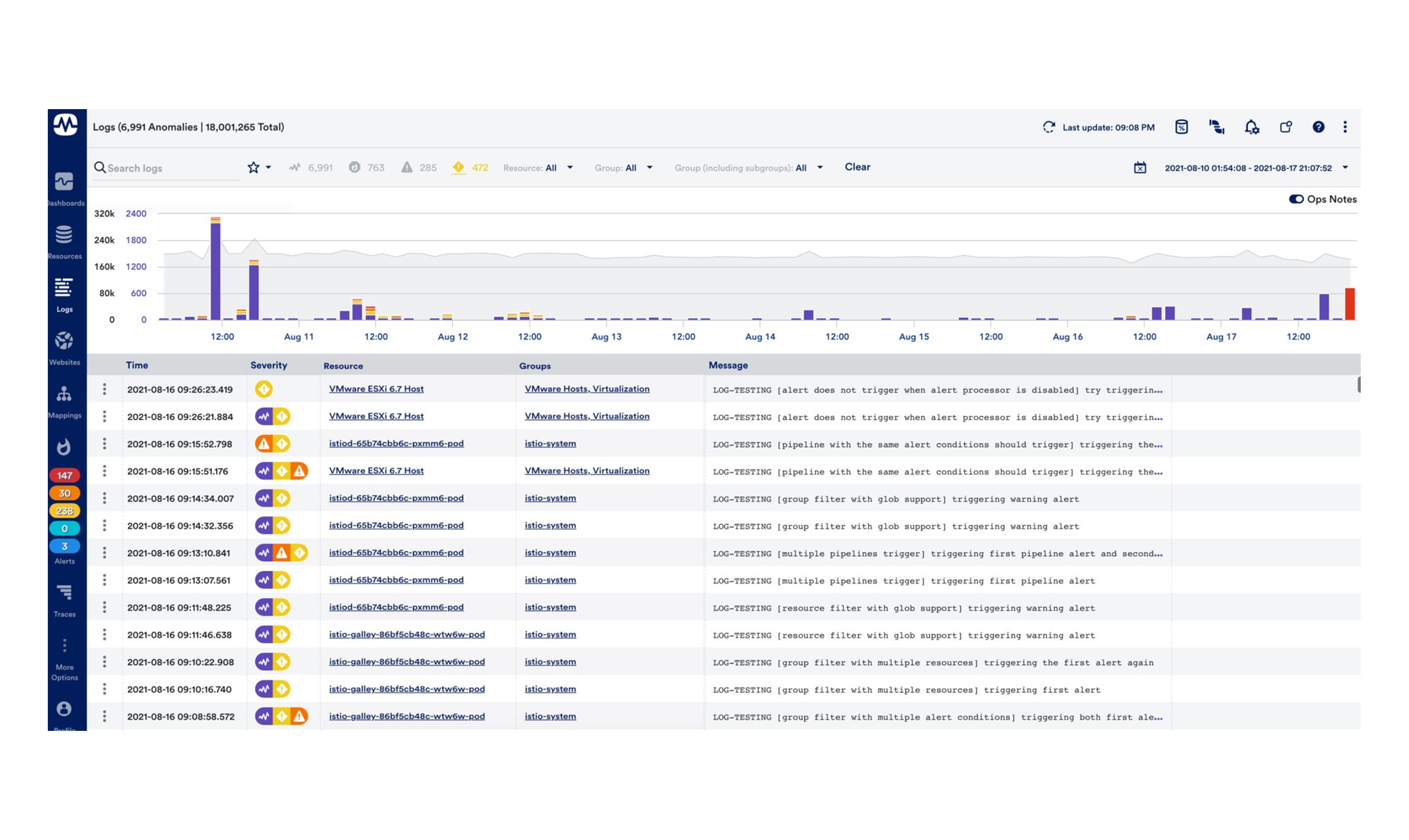
LM Logs
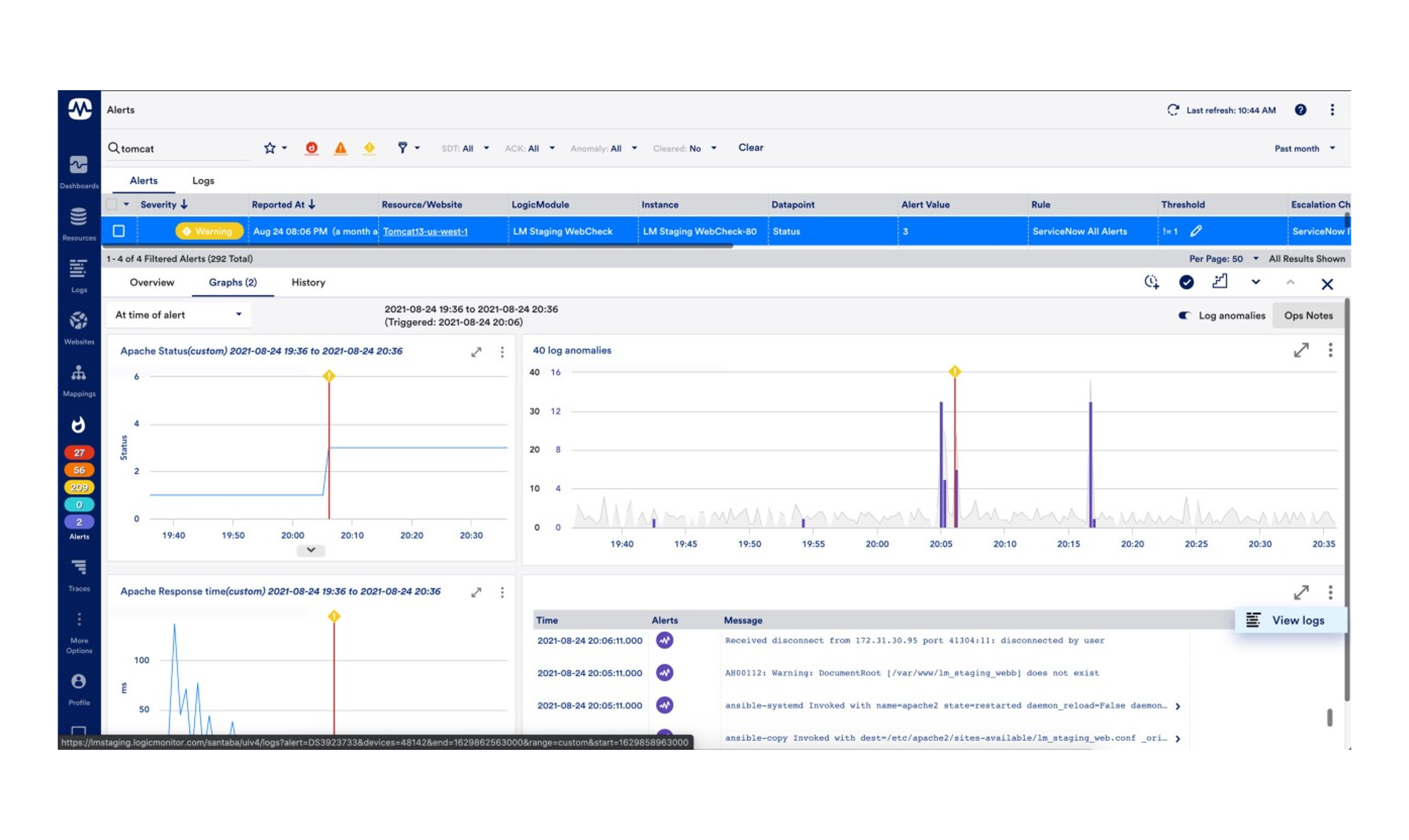
LM Logs provides a unique approach to log analysis that focuses on algorithmic root cause analysis. LM Logs analyses log events from IT environments to identify normal patterns, but also deviations from them (anomalies). By recognising these anomalies, teams can react to problems early on, before their remediation leads to significantly higher work and costs.
How to turn log data into insights
LM Logs provides large-scale log information for hybrid and multi-cloud environments, providing instant access to contextual and correlated logs and metrics in a single, unified cloud-based platform. The solution has tiered archiving options such as unlimited storage, but also a "hot storage" feature for optimal data hygiene and initiating internal compliance initiatives.
With LM Logs you can achieve:
• central processing of log and metric data in a unified platform,
• the elimination of the otherwise necessary context switch between IT infrastructure monitoring and log management views,
• up to 80% faster troubleshooting and root cause analysis (RCA) with unlimited archiving options,
• a saving of up to 40% in non-value-added development time based on ML-generated protocol anomalies.
↑↓ Navigation: LM Envision